MSIXPhish_Lab
MSIXPhish Lab
As a Threat Intelligence Analyst at a major security firm, you play a role in efficiently gathering intel about potential threats. During your work day, an incident responder has provided you with a hash associated with a malicious software installer detected in your organization’s network. Your task is to analyze this hash to gather valuable threat intelligence and enhance your organization’s defenses.
Challenge 1
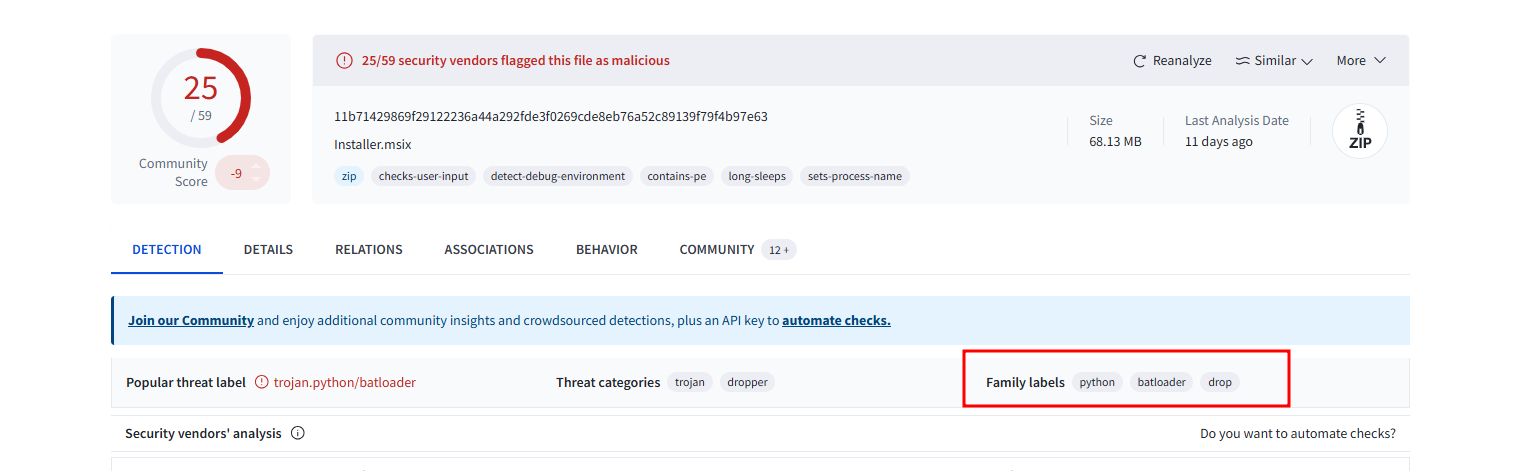
- To effectively mitigate the threat, it’s important to determine the origin or category of this malware. Can you identify which malware family this sample is associated with to better understand its typical behaviors and associated risks?> batloader
-
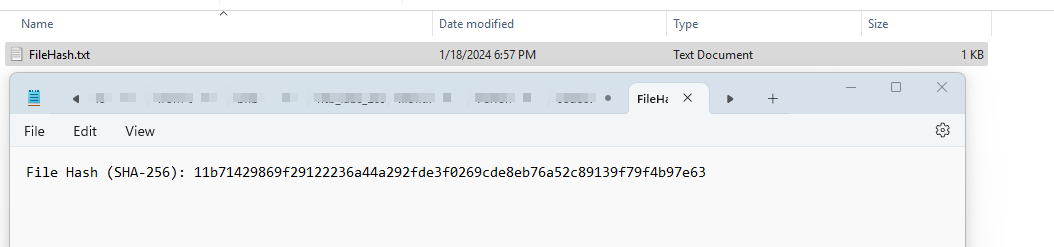
Some little background on sha sum hashes is that they are unique and can be used to identify files. In most cases, hashing algorithms take care to ensure collisions do not occur. With this info at hand, we can use this to search the files online.
-
From info provided we already know that this is a malware. Accordingly, we can therefore go ahead and search the has on virus total to identify the malware and family.
-
Batloaders are a type of malware that normally use batch and powershell scripts to gain a foothold on a target’s device to deliver malware.
Challenge 2
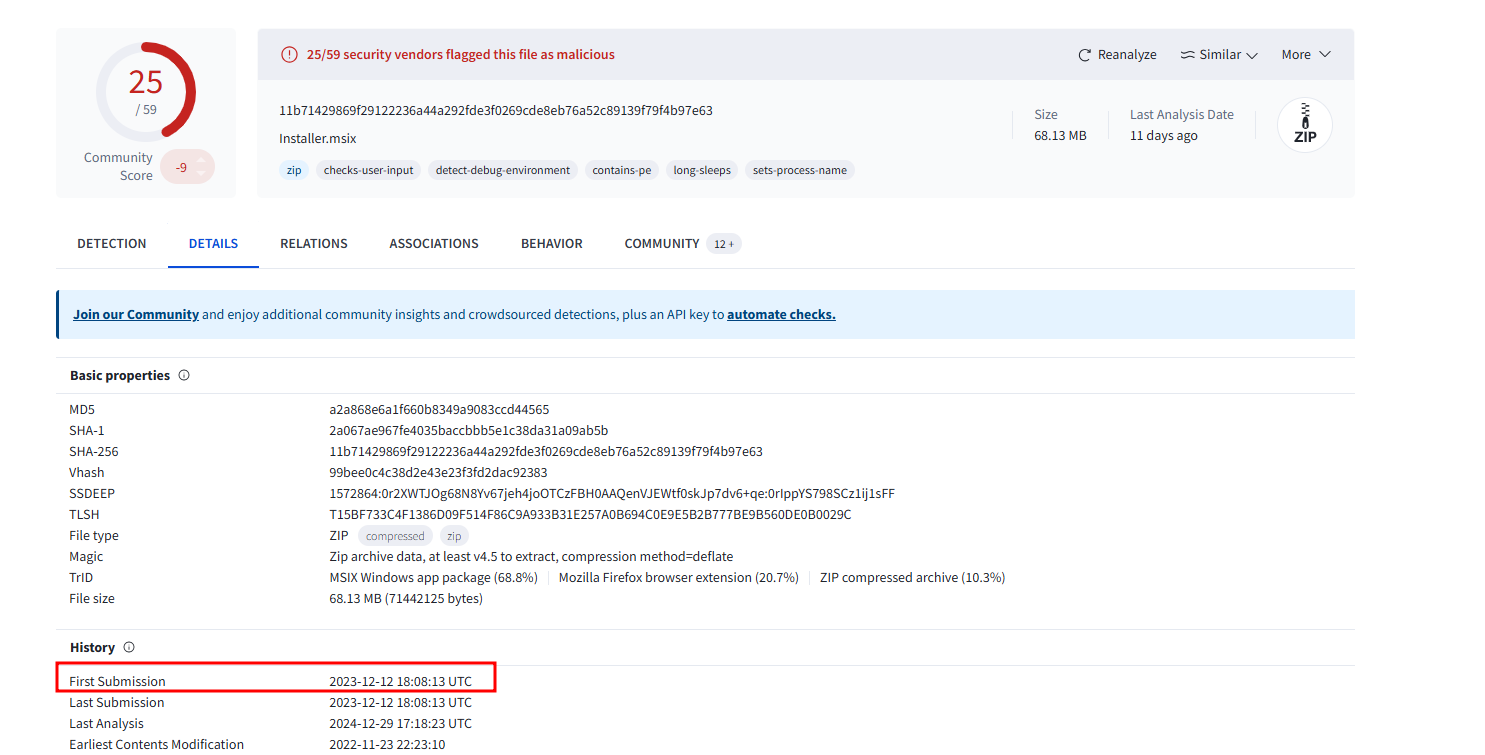
- It’s important to identify the malware’s first public appearance to effectively track its history and spread. Can you provide the initial submission date and time of this malware on VirusTotal? 12-12-2023 18:08:13
- While still on virus total, under the Details->History section, you can find more details with regards to Hashes and submissions dates
Challenge 3
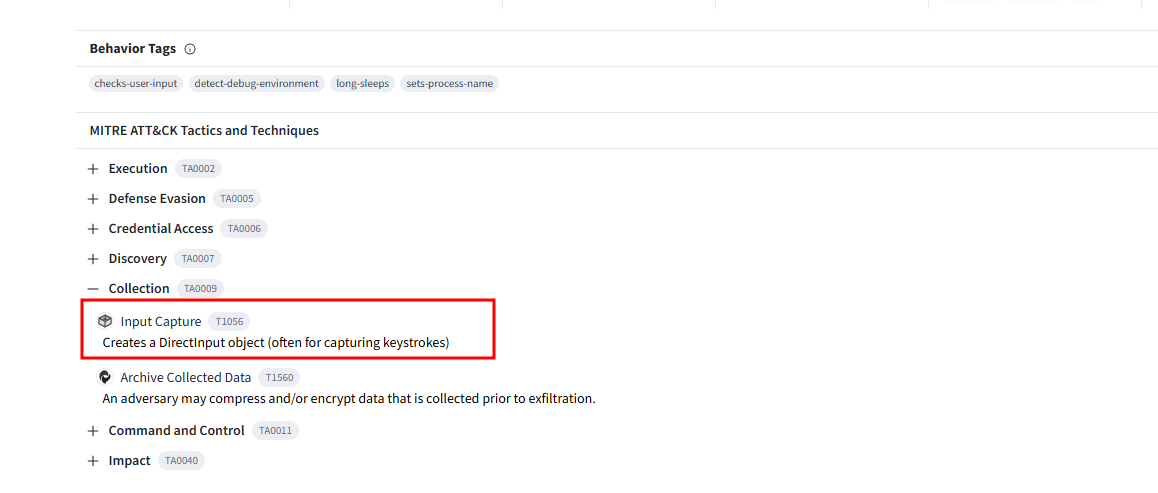
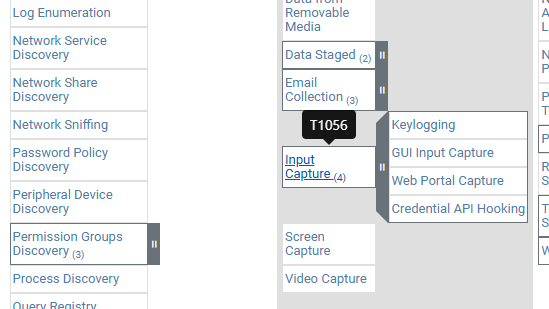
- Recognizing a specific MITRE technique employed by the malware helps develop targeted defense strategies. What’s the MITRE ID of the technique used by the malware for data collection? T1056
- On virus total under Relations -> MITRE ATT&CK Tactics and Techniques section, Find collection, where we find the malware collects data using input capture: Creates a DirectInput object (often for capturing keystrokes). This correlates with Technique T1056.
Challenge 4
- Knowing the names of executable files dropped by the malware aids in detecting and isolating infected machines.What is the name of the executable file (.exe) dropped by the malware Install.exe
- On virus total under Relations -> Files dropped, we also observer the Install.exe being dropped to the system by the malware.
- Additionally, under Relations -> Files opened, we find the file opens an executable File Install.exe, from the directory: C:\Users<USER>\AppData\Local\Temp\
- This further confirms that the malware is under the batloader family

Challenge 5
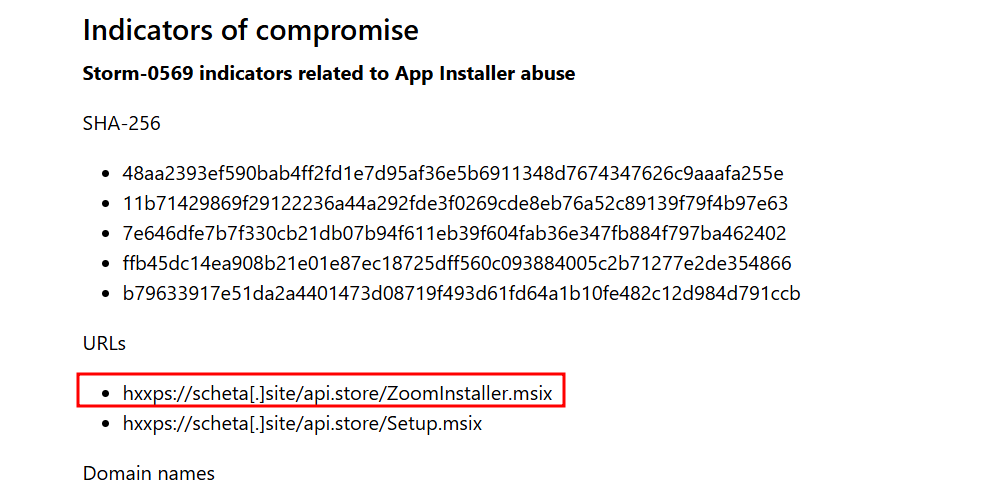
- Continuing on the previous question. Can you identify the name of the second execution parent observed in the wild for the executable discovered in the previous question? ZoomInstaller.msix
- On virus total under Community, we can find further analysis from the community, whereby in this case, we find a report about the malware.
- In the report, we find a url being contacted by the domain and an msix file would be fetched.
Challenge 6
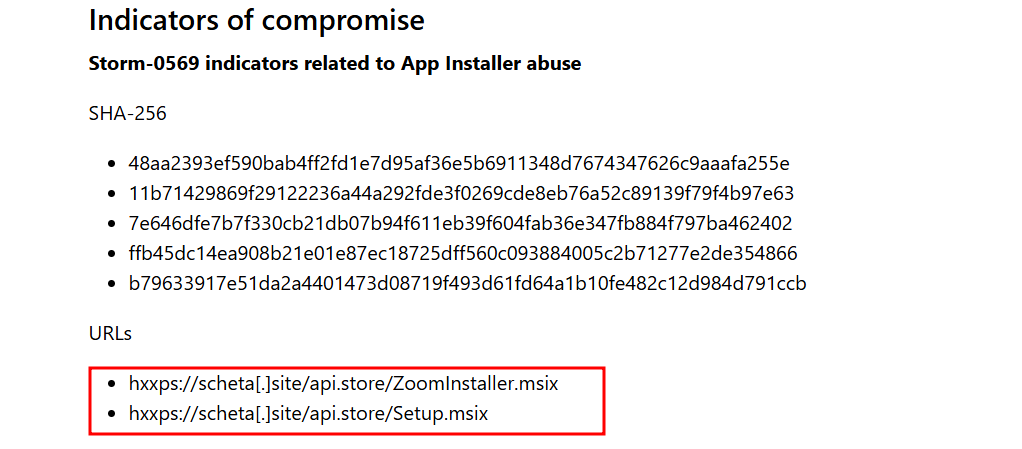
- Identifying the domains used in attacks can help block future malicious communication and understand attacker infrastructure. What domain is used by the threat actor to host the illegitimate application installer? scheta.site
- On virus total under Community, we can find further analysis from the community, whereby in this case, we find a report about the malware.
- In the report, we find the url being contacted by the domain was: scheta.site.

Challenge 7
- We need to identify the access vector abused by the malware to mitigate it. What protocol handler is exploited by the malware?
ms-appinstaller
- From the community link, we find that the installers and threat actors are utilizing ms-appinstaller URI Scheme for the downloads.
- This is a protocol that can be used to install an app directly from a web server, which in this case this was an attacker controlled server.
Challenge 8
- Uncovering the threat actor associated with this malware is key to understanding their tactics, techniques, and procedures (TTPs) and bolstering defenses against future attacks. Can you provide the name of the threat actor? storm-0569
- From the community link provided, and IOC identified during our investigation, storm-0569 tends to have files with the same has as our identified file.
- Additionally, the urls contacted and files download match with our file. i.e. zoom installer, scheta.site etc.
Conclusion
-
Attackers may exploit installation of software from web servers in the network using i.e. ms-appinstaller protocol. This protocol can be disabled on the network by setting the Group policy EnableMSAppInstallerProtocol (/windows/client-management/mdm/policy-csp-desktopappinstaller) to disabled if this is not needed on the network.
-
IOCs for this line of batloader malware can be detected using the query:
DeviceNetworkEvents
| where InitiatingProcessCommandLine == '"AppInstaller.exe" -ServerName:App.AppX9rwyqtrq9gw3wnmrap9a412nsc7145qh.mca' and RemoteUrl has_any ("https://", "http://")